pfSense is one of the main tools I use for firewalls. My SMB customers benefit greatly from the features of pfsense.
If you have some extra hardware lying around, you can build yourself a pretty nice pfsense box. Mine: Core i5 3.1 GHz, 16 GB DDR3, with 4 network adapters, all packed into a desktop case that I built in 2012. I could have purchased an appliance that runs pfsense; for example, the SG-1100 would have suited my needs as it has LAN/WAN/OPT ports. But compare the specs. That device ($159 when this article was published) has a 1.2 GHz ARM-based CPU with 1 GB of RAM (SOC configuration). Now, if you are working for a company that wants a hardware warranty and/or support, then an appliance is the way to go, and the software works the same way. However, if you have a smaller business or a lab, building your own is a great way to recycle an older PC--that perhaps has a tough time running today's desktop operating systems--and save money at the same time.
I like pfsense, as it is open-source, has a solid design, and a lot of features. For a small company who is tired of poorly made SOHO routers from the big manufacturers, this can be a big improvement--whether you use an appliance, or build your own. It is built on FreeBSD, which is one of my "go-to" tools for files servers and NAS solutions. It's one of those types of systems that can potentially run for years without interrruption of any kind.
The video below shows a PC I had that was a media server which I re-purposed into a pfsense system.
Video
Network Design
The figure below shows the interfaces and IP networks I am using with this system:
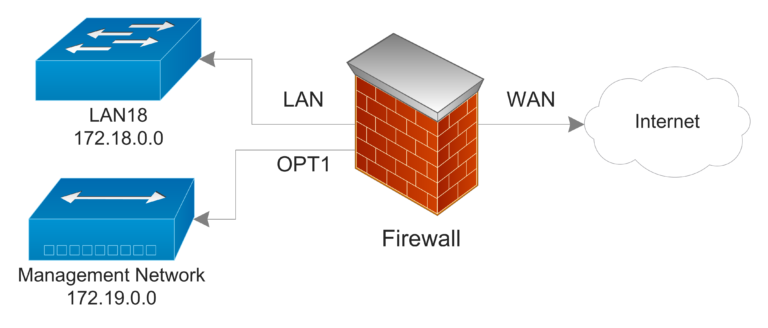
The firewall is the Core i5 PC with pfsense installed. It has three network interfaces: LAN, WAN, and OPT1.
The LAN interface is a dual RJ45 NIC that I configured to use link aggregation. It connects out to a Cisco switch where I have several servers including a virtualization server with with a bunch of VMs--it is all on the 172.18.0.0 IP network.
The WAN interface is a single RJ45 NIC which is assigned a public IP. (I have a bank of static public IPs that I get from my ISP. If you are obtaining an IP automatically, no configuration is necessary for this interface.)
The OPT1 interface (optional 1) is an integrated RJ45 on the motherboard of the PC. That connects to a separate switch used for management of my servers and devices. Any server with a dedicated management port (IPMI, or otherwise) connects to this switch. This is essentially another local area network, and is on the 172.19.0.0 IP network. I use the OPT1 interface to make configuration changes to the firewall. However, it was not possible to do so until I logged in on the LAN interface, added the OPT1 interface, and added a rule to the firewall that would allow me to remotely connect via that OPT1 interface. Once that was done, I could remotely manage the pfsense box without using any of the bandwidth of the LAN interface. Plus, it made it a lot easier to setup link aggregation on the LAN interface, as I was connecting separately.
Final Thoughts
If you are a individual, or a small to mid-sized business, consider this: Data transfer between the LAN and WAN interfaces is substantially faster than with a typical SOHO router, and with less dropped packets. The better the device, the better pfsense runs for the most part. Also, it sees hardware like a champ. It didn't miss anything in this PC.
In summary, I like pfsense. Do your self a favor and check it out.

